Kivera Policy Reference
Every service, action and parameter that can be controlled through Kivera
Already a Kivera User?Product documentation for existing users is available here - https://docs.kivera.io/
Overview
Kivera is a next generation cloud security solution that prevents cloud misconfigurations at both build and run time. Kivera operates with multiple enforcement modes including preventative, preventative-learn and detective. Kivera's policy engine deeply understands cloud API requests allowing enforcement to occur across any cloud service regardless of how it is consumed.
This policy reference is automatically generated from the cloud provider API specifications and adapted into Kivera policies. As new services, features and parameters are released, this reference will be updated and acts as a repository of hundreds of thousands of controls that can be enforced through Kivera.
Preventative Cloud Policies
The policy reference provides Kivera policies for every service across AWS, Google Cloud and Microsoft Azure. These policies apply directly into Kivera allowing control enforcement on over 250,000 individual API request parameters.
Combining these parameters with Rego functions provides incredible granularity, depth and flexibility over your cloud.
Policy Evaluation Overview
Kivera's preventative engine operates in a allowlist mode ensuring that an individual API request meets all required policies before proceeding to the cloud provider API. For example, if you wanted to enforce that upon creation, every AWS SQS Queue had encryption enabled, you could use the following policy:
valid {
input.Body.Attribute.KmsMasterKeyId == "alias/aws/sqs"
}If an API request was made to AWS without the KmsMasterKeyId present, the request would be blocked by Kivera. This policy can be found as a stub in our policy reference.
Action Filters
Kivera also supports API action level filters which makes it easy to allow broad sets of actions through Kivera using specific actions e.g. CreateQueue, DeleteQueue or wildcards e.g. List*, *List, Get*, *Get etc.
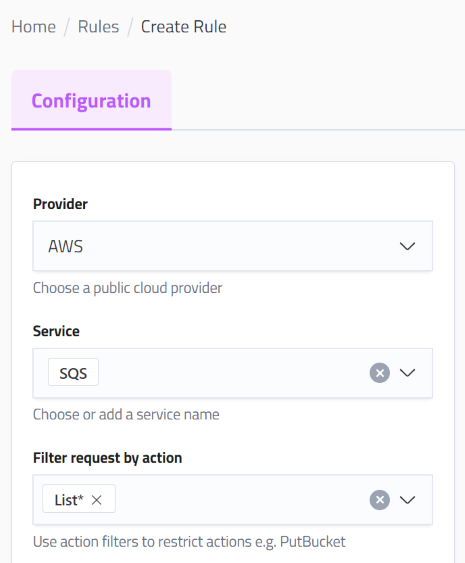
Allow all calls if the API action begins with 'List'
Updated 4 months ago